Development and demonstration a Trusted Web related prototype system for the proof of identity and existence in the case of an online subsidy application for Solo proprietorship and Small and Medium-Sized Company(DENTSU.INC)
This page shows the "Development and demonstration a Trusted Web related prototype system for the proof of identity and existence in the case of an online subsidy application for Solo proprietorship and Small and Medium-Sized Company" exploried and tested by DENTSU.INC, in the 2022 "Use Case Demonstration Project of the Trusted Web".
Please click on the links at the bottom of this page to learn more about the details of the demonstration.
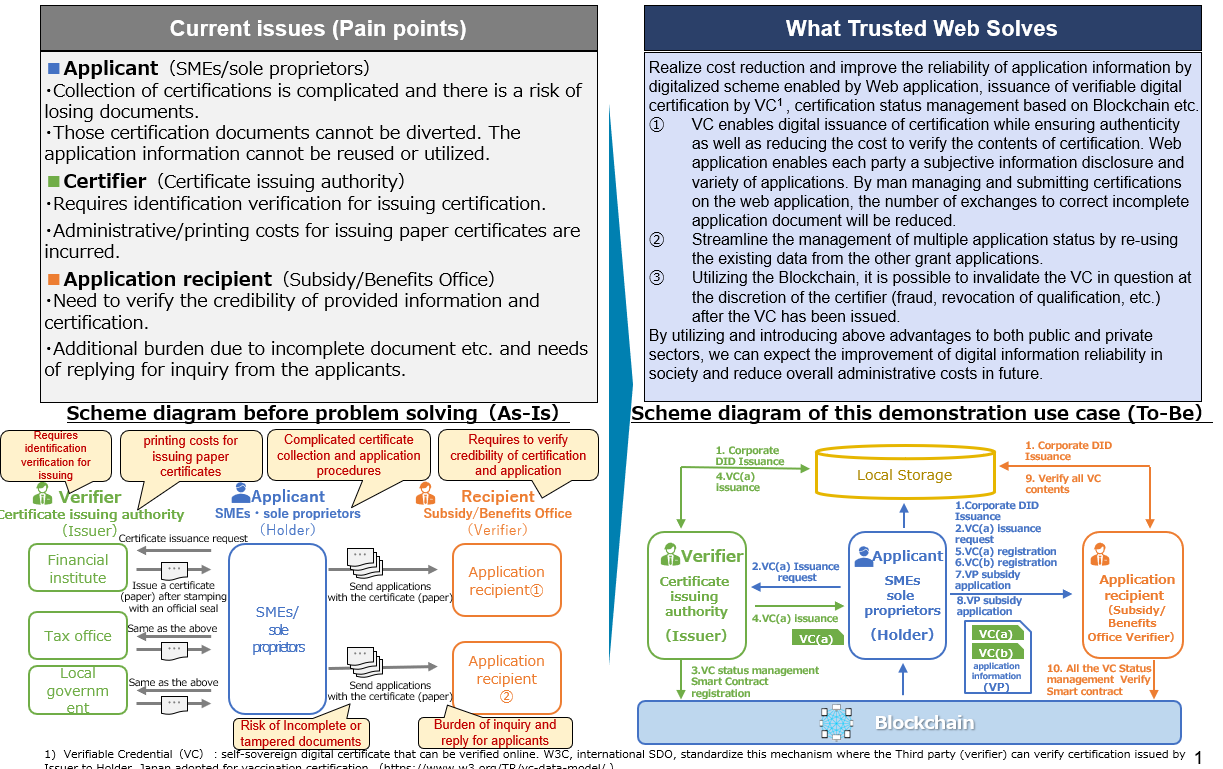
Current issues and What Trusted Web Solves
Data to verify
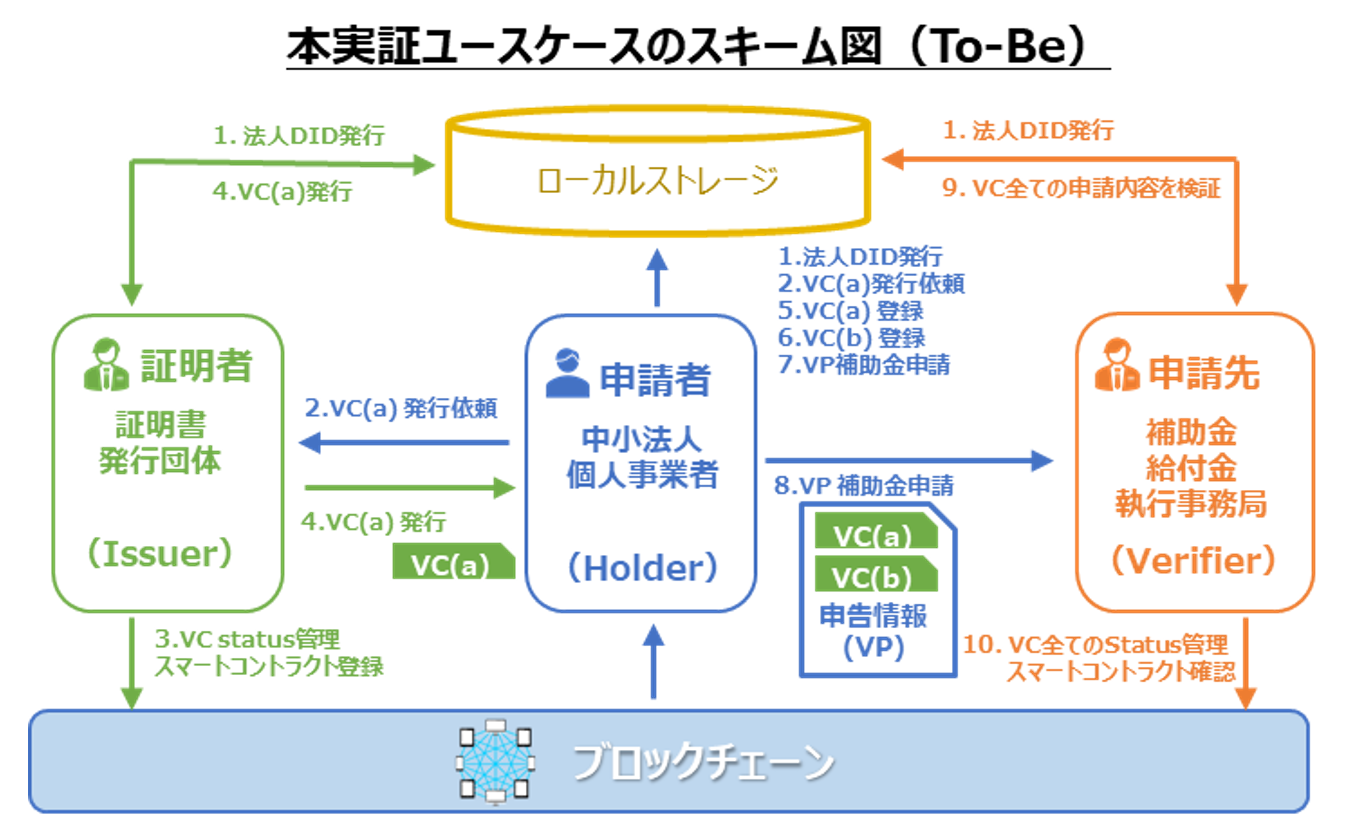
■Spoofing of applicants and falsification of application contents
In order to check for applicant impersonation, the issuer of the application documents is verified by VC signature verification. Specifically, all the VCs received by the Benefits Execution Office are verified by EdDSA1 signatures.
In addition, the interactions between each entity other than the VC are verified by JWS2 signatures. Signature verification enables us to check where the issuing authority is and whether the contents have been tampered with, thus expanding the area that can be verified.
- Legitimacy to be verified:Verify sending data against tampering by signature on the data.
- Object of verification (data/data transaction):Interaction between entities as well as VC is verified by signature.
- Verification Method:Verified by EdDSA and JWS.
- Verifier:(Application) recipient and all the data recipients.
- Data ownership:Certifier and applicant (VC), applicant and application recipient (VP).
- Issuer:Local governments, financial institutions and tax office (certifier).
- Data (VC) storage:Currently, stored on local storage.
- Access control method:In the future, only the sender and recipient will have access to the message.
- Results/Notes:Signature verification enables to extend the area can be verified.
1)One of the digital signature (technology for proof of identity and prevention of falsification of electronic data) of Public-key cryptography.
2)JSON Web Signature (JWS). Technology standard for digital signature on files of JASON, type of data description language.(https://www.rfc-editor.org/rfc/rfc7515)
Achievements
- In a technical study to digitize the conventional grant and benefit application process through a mechanism utilizing the Trusted Web, identification and proof of existence, which had previously been done by attaching paper certificates or scanned data, was implemented by verifying the EdDSA signatures on the Residence Certificate VC, Account Existence Certificate VC, and Tax Payment Certificate VC. As a result, we successfully confirmed that the issuing authority and contents of the VC had not been falsified, and confirmed that the implementation was technically feasible. Necessity to consider more efficient ways such as remote identification and linkage with existing KYC method including private service was confirmed.
- To study business models, based on results from interview with stakeholders, we propose following:①Pros and Cons of digital certification (reducing cost and increasing burden of system operation) ②Benefits such as certifier’s income from service fee③Importance of the efforts to create an ecosystem and the cost of transition from an analog (paper)-based world.
Documents
To communicate with Trusted Web stakeholders,
please use the contact form.